IBM has published its annual report on the cost of a security breach for the year 2023. In it, it is indicated that the costs have experienced an increase with respect to the year 2022, reaching a historical maximum since the beginning of the publication of these reports .
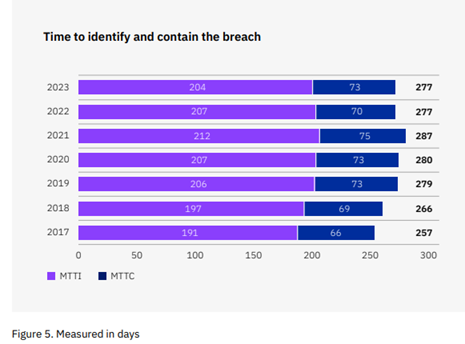
The report reveals that the average time to identify and contain a cybersecurity breach is not around a few days or weeks, but is currently 277 days, that is, more than 9 months for an organization to detect that it was violated and mitigate the effects.
The report also shows that the use of certain technologies and good practices makes it possible to reduce these detection and mitigation times, based on the responses of the more than 500 companies involved in the study.
Many of these supports in improving detection and mitigation conditions are those that we propose from the Blue Team unit and that we have operating in our SOC and Managed Cybersecurity Services.
First of all, the graph indicates that an organization working with a Managed Security Service Provider (MSSP) significantly reduces the time involved in incident management.
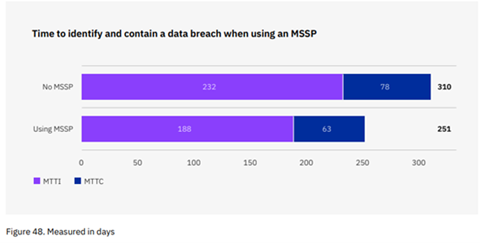
At INSSIDE, as MSSP, we offer organizations the ability to outsource cybersecurity management, through SOC services and Managed Services with 24×7 operation.
In addition to the usual services we provide from our Operations Center in Buenos Aires, we have launched a new SOC, located in Honduras, through our partner GRUPO POPA. This SOC allows us to have a local presence in Central America with the benefits of operating in similar time zones, on-site presence if required, and infrastructure within the country, in case of regulatory requirements that require it.
Identifying and containing a breach using security AI and automation took just 66% of the time it took for organizations without its use.
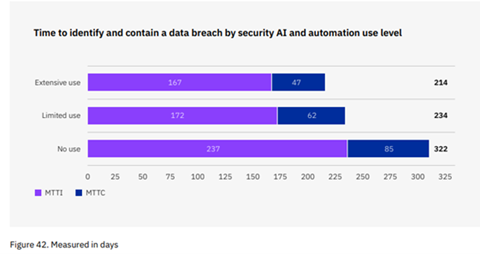
It is clear that even a limited effort to integrate AI and security automation into security workflows can offer significant acceleration in time to identify and contain a breach, as well as a significant reduction in costs.
Our SOC infrastructure is based on IBM QRADAR as the SIEM platform, and on Palo Alto’s CORTEX as the SOAR platform, enabling the automation and orchestration of incident response in machine time, rather than executing response in operator time human who must follow a checklist or execute a paper playbook.
Other technologies that are presented as improvements in detection and mitigation processes are: Threat Intelligence, Vulnerability Management Processes and ASM (Attack Surface Management), which are solutions and services that we provide from our SOCs and that we can consider within a comprehensive proposal to our customers.
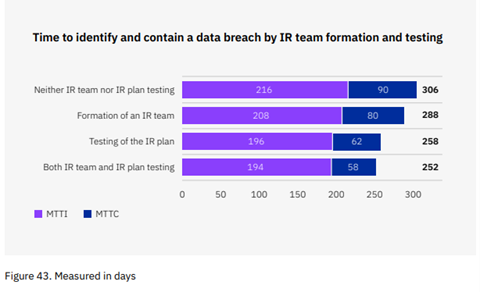
The dual strategy of building an IR team and testing an IR plan demonstrated a shorter time, 252 days, to identify and contain a data breach compared to 306 days using neither approach, a difference of 54 days or 19 ,4%. Testing the IR plan without building a team was almost as effective, resulting in a difference of 48 days or 17%.
As we can see through the results of the IBM report, the benefit of integrating SOC services and Managed Cybersecurity Services within the organization’s strategy is clear.
At INSSIDE Cybersecurity we work with market-leading technologies to create safer environments that increase and mature the cybersecurity of organizations, in order to manage and reduce the risk that may impact situations of unavailability of services, financial fraud and/or impact on the reputation of the brand.
For more information contact INSSIDE

